The LSM RAM Agent CLI (Command Line Interface) can be accessed:
•Locally, from the Machine's local console:
oAfter executing the Payload Stage LSM RAM Agent CLI As Root script or equivalent
•Remotely, from the LSM Server's command line using SSH:
oAfter executing the Payload Stage LSM RAM Agent CLI As Root script or equivalent, or
oIf the Machine's Payload Service Completion Pause Option has been set to PauseWait.
Warning: granting access to the LSM RAM Agent CLI is potentially very dangerous, as the CLI User can alter/damage/destroy not only the Machine contents but also User Snapshots and Files on the LSM Server.
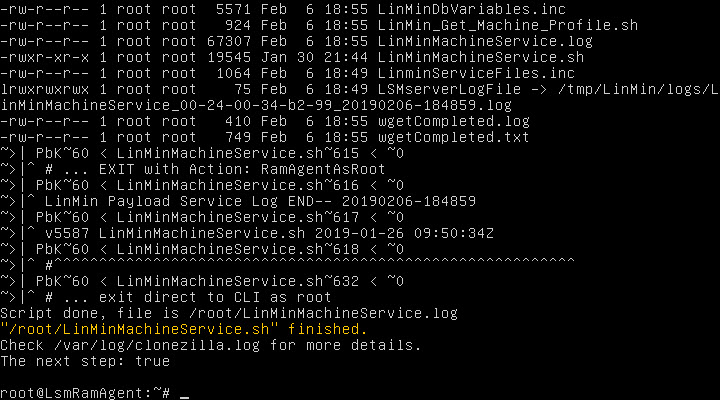
Local access to the LSM RAM Agent CLI from the Machine's console
After the profile has been captured, the Machine will present a screen similar to this:
The shell presented is a subset of standard Ubuntu bash:
Remote access to the LSM RAM Agent CLI
LSM RAM Agent password for User "ramagent": live
From your LSM Server CLI, use ssh with the Service IP of the Machine you wish to access:
# ssh ramagent@192.168.49.129
The authenticity of host '192.168.49.129 (192.168.49.129)' can't be established.
ECDSA key fingerprint is SHA256:aLj6o0QifNibYcJx+Z1ypdFxBk2q4vmoHm2KpcolWGA.
ECDSA key fingerprint is MD5:ac:0c:fb:df:af:46:98:1a:f4:66:76:d7:0b:d0:87:98.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.49.129' (ECDSA) to the list of known hosts.
ramagent@192.168.49.129's password: # note: enter the password live
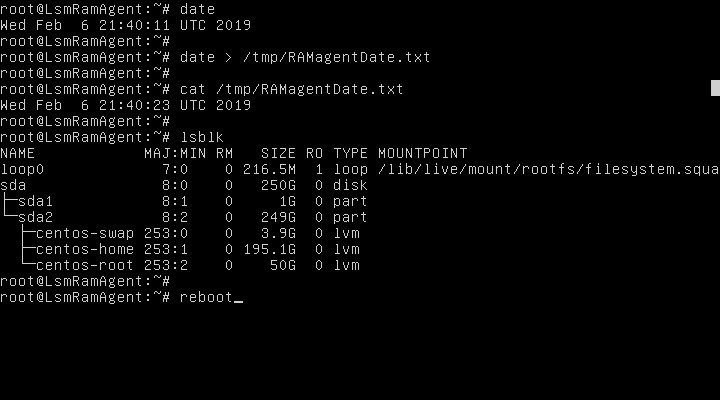
ramagent@LsmRamAgent:~$ lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
loop0 7:0 0 216.5M 1 loop /lib/live/mount/rootfs/filesystem.squashfs
sda 8:0 0 250G 0 disk
├─sda1 8:1 0 1G 0 part
└─sda2 8:2 0 249G 0 part
├─centos-swap 253:0 0 3.9G 0 lvm
├─centos-home 253:1 0 195.1G 0 lvm
└─centos-root 253:2 0 50G 0 lvm
ramagent@LsmRamAgent:~$ exit
logout
Connection to 192.168.49.129 closed.
[root@rhel7-lsm70 ~]#